Using ophcrack in Kali Linux / Backtrack to Crack Hashes
Ophcrack is GUI tool that can be used for the purpose of cracking password hashes. Perhaps the main attraction of using this tool is its ability to deploy rainbow tables while cracking the password. This makes the process of brute force cracking faster.
At this point, it is essential that you understand the importance of rainbow tables in a brute force attack. As you know, a hash is a one way function and cannot be reversed. So we can’t convert the password hashes back to their corresponding plaintext forms. For this reason, during a brute force attack, we take a potential passphrase (in plaintext) and convert it to its hash form. Then we can compare this hash with the password hash and if there is a match, we know that this plaintext is the passphrase. Basically, during a brute force attack, a lot of time and CPU power is wasted in computing the hashes. Rainbow tables are ‘pre-computed hashes’. So once you have a rainbow table, all you need to do is ‘compare’ the hash in the rainbow table to the password hash you have obtained during penetration testing. Hence, you save considerable time and CPU cycles while hunting to the plaintext form of the passphrase.
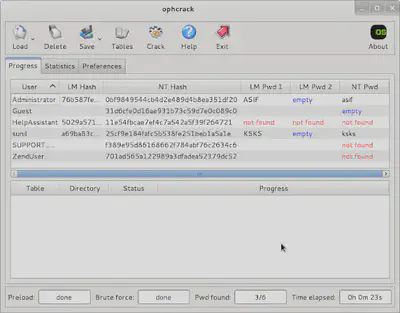
Here’s an example where I cracked some LM Hashes I grabbed from a machine during penetration testing (the hashes were obtained by using pwdump in Meterpreter).
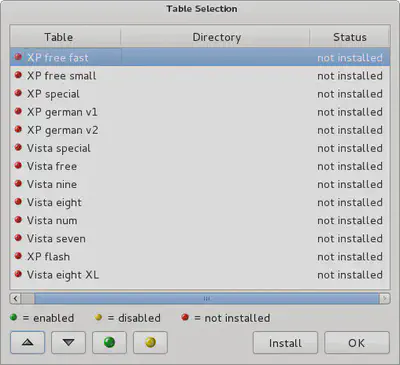
You can load up any of these rainbow tables germane to the victim’s OS. Click on ‘install’ to obtain them. They are large files and will take a while to download depending on your network bandwidth.
Ophcrack can speed up the Windows password cracking process during penetration testing, and if you test Windows system frequently, it would be prudent to have these rainbow tables saved on your local disk.