KringleCon | Python Escape from LA | CTF Challenge Solution
Python Escape from LA
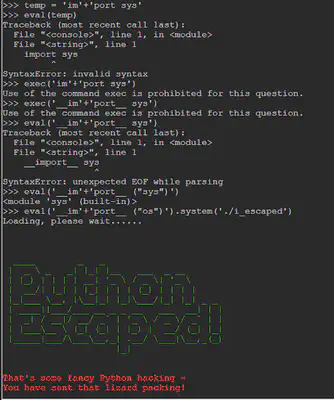
This challenge is about breaking out of a restricted shell to execute a program that resides in the directory. In this case, we are provided a Python shell but we cannot import any modules that would let us perform advanced tasks such as executing a binary. The administrators have tried to ensure this by implementing what looks like a blacklist of words such as import and exec.
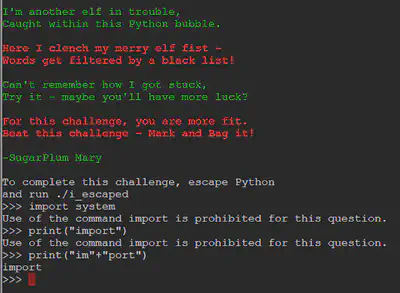
Playing around with the possibilities, we see that while print("import") would trigger the block on the word import, we can get around it the block with print("im" + "port") as shown above.
We know that import and exec are blacklisted, but eval() is not! So if we can get eval() to import the os module, we can then execute the binary. However, eval() works only on expressions but import is a statement. So in order to counter this, we can try __import__ ("os")
We can see that we are now able to successfully import the module os. It is pretty straightforward after this point. The following expression will allow us to execute the binary:
>>> eval('\_\_im'+'port\_\_ ("os")').system('./i\_escaped')