KringleCon | HR Incident Response | CTF Challenge Solution
Question 7 HR Incident Response
In this challenge, we are given a website with CSV upload capability and are asked to somehow gather information from the contents of the file: C:\candidate_evaluation.docx. Since the website allows CSV uploads, we can try some CSV injections to see if we can access the contents of the DOCX file.
Now the file is stored in the root directory of C drive on a Windows system. To be able to access its contents, we need to “move” it to a public directory visible over the web. If we try to access a non-existent file then we are given the following error message.
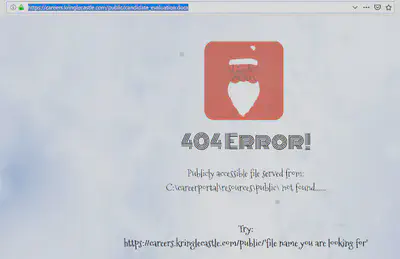
This unnecessarily descriptive error message tells us two things: 1) the DOCX we are looking for does not currently reside in the /public/ directory, and 2) the absolute path to the /public/ directory is: C:\careerportal\resources\public\
So now we try to “move” the DOCX from the root directory to the public directory where we can access it. However, thinking about it, moving a file like that is more problematic in terms of permission issues. It is easier to just copy the file to the public directory. Now that we have an idea of what we need to do, we can move on to actually implementing it in terms of a CSV injection.
Our CSV injection only requires a simple copy command that will execute on the Windows system on the server side and perform the necessary copy operation. So let us create the following CSV file in a text editor:
\=cmd|'/C copy C:\candidate_evaluation.docx C:\careerportal\resources\public\whothis.docx'!A0
A glitch I noticed in the way the CTF challenge was setup was that if there’s a space between the \=cmd| and the following ' (single quote) in the injection shown above, then the copy would not work on the server. However, when tested on a local Windows system, it works perfectly fine whether or not the space is present. For the sake of the challenge, we do it without the space and upload this CSV on the career portal website. After a few seconds, we are able to access the DOCX file in the public directory which indicates that the CSV command injection succeeded on server side.
I did not trust to open the DOCX on my local system, so I converted it to a PDF online and opened the resulting PDF which contained the sensitive information we needed to progress to the next challenge.
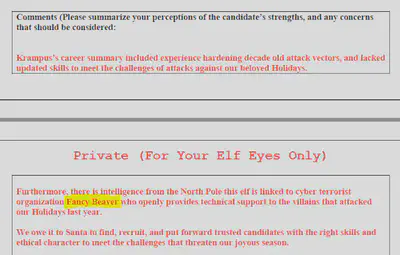
Password: Fancy Beaver