How To Test Cookie / Session ID Randomness Using Burp Suite Sequencer
When you log on to a web server, a session is created which is identified by a session ID. The session identifier can be a cookie. This cookie holds the session ID so that one can log in once for each session (From there on, the session is then passed on to various web pages one browses on that server). Read up on Session Management.
Session, hence, depends on the session ID. In PHP, the ‘PHPSESSID’ holds the session ID when you visit a webpage on the server.
This needs to be random enough to preserve the security of the session. If an attacker is able to estimate what the session ID is going to be, he/she can bypass authentication.
Test for Randomness of the Session ID / PHPSESSID / Cookie | Mutillidae
Attacked Server: Mutillidae
Test Page: Main Login Page
Test Parameter: PHPSESSID
Test Type: Session Randomness
- Load up the web page on the server and intercept the request in Burp Proxy. Now notice the server sets the PHPSESSID. Delete this and forward the request to server.
The server notices the mission PHPSESSID and sets a new ID.
Now delete this and right click ‘Send to Sequencer’
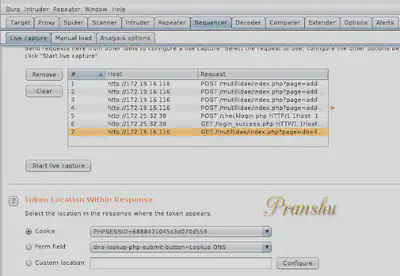
-
In the sequencer make sure PHPSESSID is highlighted for testing and being the test > ‘Start live capture’
-
The test will keep grabbing new tokens and then analyze this sample data for randomness.
For accurate results wait until sample size is at least 200 tokens.
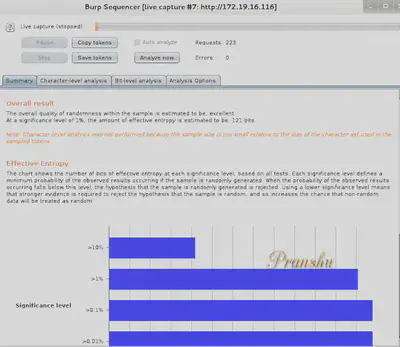
Then click ‘Analyze Now’
Notice the Entropy is 121 bits which is ’excellent’ (entropy refers to the randomness)
So this test ensures the unpredictability of the Session ID