How To Spoof DNS In Kali Linux
Facebook Phishing Page Using Social Engineering Toolkit In Kali Linux
I was recently asked to demonstrate quickly how DNS can be spoofed using Kali Linux, and how the traffic can be forwarded to a fake phishing page. I decided to demonstrate by phishing the Facebook page and spoofing the DNS to point facebook.com to my machine’s IP address where I am hosting a fake page using social engineering toolkit.
Here’s the procedure:
Host a phishing page using se-toolkit: Website Attack Vectors -> Creditials Harvestor -> Clone website / Use Web Template
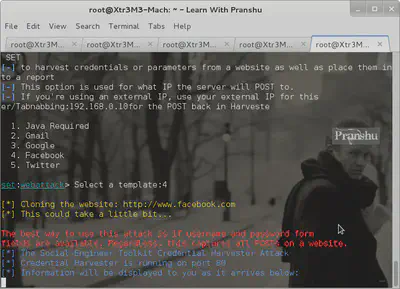
As you can see I used a template of Facebook and SET hosted this on my IP: 192.168.0.10 at port 80.
Now I need to make sure traffic meant for facebook.com is redirected to my IP, for that I can use a DNS Spoof plugin available in ettercap
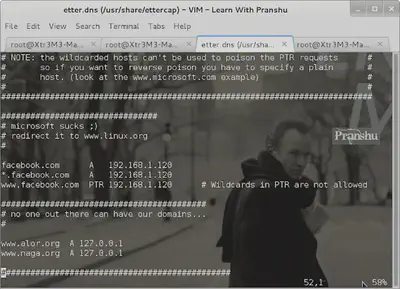
Change the contents of the file etter.dns, so the facebook.com points to your own IP.
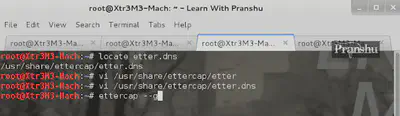
Then load up “ettercap –g” and goto Plugins -> Manage the Plugins -> double click DNS Spoof plugin. Make sure you see the ‘*’ next to it
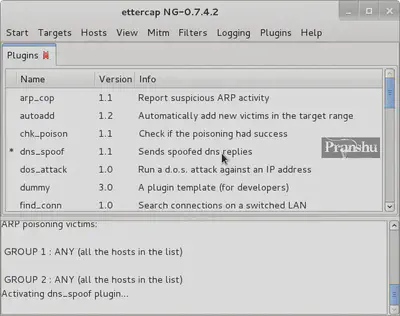
Next, ARP poison all the hosts in the network, so that all the traffic passes through your machine. Start sniffing (read up on ARP poisoning if you can’t understand).
Wait for the sometime. When someone tries to access facebook.com then your ettercap window will tell you ‘blah_blah.facebook.com’ spoofed to <your ip>.
At the same time in your SET window you’ll see ‘we got a hit!!’ along with some other info. If the victim is gullible enough to enter his/her credentials on your phishing page, you’ll see those details in the SET window.
But you have to play the waiting game and hold on until someone tries to access the phished website.

Disclaimer: This Post was only to demonstrate a concept; no Facebook hacking is endorsed or intended. This will only work on internal networks, that is, machines susceptible to your ARP poisoning attacks.