Fuzz Testing Web Applications With Burp Suite | Burp Intruder [Sniper] to Fuzz Parameters
IronGeek hosts a lot of good videos about testing web applications with Burp Suite. I tested these attacks out myself.
Attacked Server: Mutillidae
Test Page: Main Login Form
Test Parameter: Username
Test Type: Fuzzing
In simple words, fuzzing means sending “weird” data to the server and observing how it reacts to it. More formal explanation can be found here.
Fuzz Testing Login Form Parameters using Burp Suite | Mutillidae
-
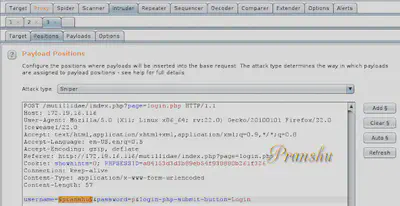
Enter any username on the web page, press enter and intercept the request in Burp Proxy. Then send it to “Intruder”
-
Select the “sniper” attack type in Intruder and select the username parameter to be fuzzed [marked by $..$]
-
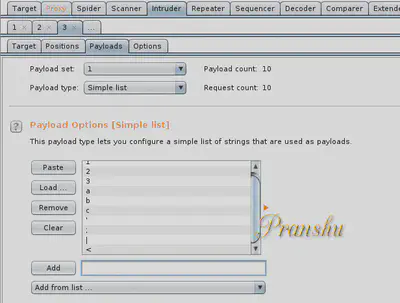
Now time to set the ‘Payload’, that is, what that random data is going to be. For test purposes, I used a simple list where I inserted payload manually. You can use various fuzz lists available on the Internet.
-
Notice one of the fuzz payloads is
'
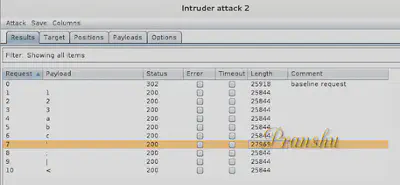
- Click Start Attack. And after it finishes notice the server response page. HTTP Codes are
200 OK. And the length of the returned pages (server response) is of interest.
Almost all response page lengths are the same, except the one for the payload '
‘Render’ this page in Burp and you will see that the page is greater in length because it returns additional error lines (database error, SQL injection attacks possible)
So the fuzz test revealed possible SQL injection on the login form on parameter username.