Driftnet Tutorial | How to Sniff Images with Driftnet + Arpspoof / Ettercap | Kali Linux
If you’re on a shared LAN and you are curious to know what kind of images people are searching for over the web on your Local LAN, you can use Driftnet.
For a penetration tester, there’s no direct point of doing this, but since I tested this, I thought I might as well make a post about it. As a network administrator who is enforcing a policy on what kind of images are being searched on the local network, this might come in handy to see what images people are viewing at any time.
How to Sniff Images using Driftnet | ARP Spoofing with Arpspoof or Ettercap in Kali Linux
If you are learning, it is better to use Arpspoof to do the spoofing since it’s a manual command line tool and if you set up the man in the middle attack in this manner, it will aid your learning.
- Enable IP forwarding
echo 1 >> /proc/sys/net/ipv4/ip_forward
- Use Arpspoof on the desired interface [eth0] to spoof local switch’s MAC to your own for a particular Victim IP in the network [see Figure below]

Victim machines now think you are the switch, hence all packets destined for the switch arrive on your machine.
- Use Arpspoof to spoof the victim’s MAC to your own for the switch on the network.
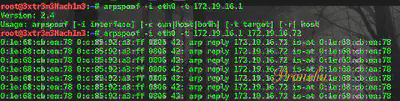
Traffic from switch destined to the victim’s IP now arrives on your machine.
You are now acting as the “man in the middle”
- Fire up driftnet. If you’ve done it all right, you should see the images
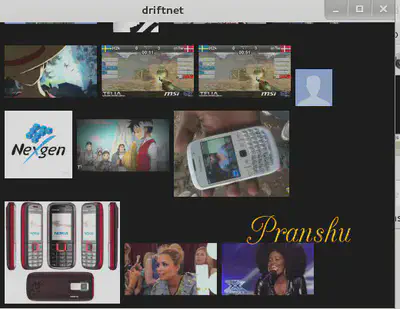
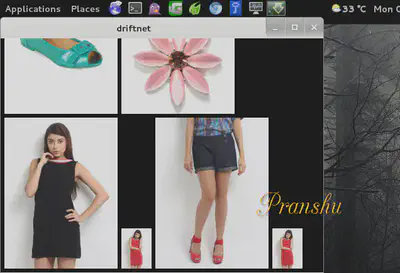
Looks like someone’s hunting for a new dress.
Using Ettercap to perform the ARP Spoof
This is a GUI tool, and ARP Spoofing using Ettercap is simply point and click a few times. There are several tutorials on it on the web, so I am not covering that. But the concept is the same Man in the Middle Attack.